True, other than try and steer clear of them ,there is little one can do for a phish attack.Surely, there are tons of advise on how to guard from phish.Whats more, security companies are making money out of identifying and flagging phish sites.
Now that makes me wonder...Is there no other go? Reminded me of the "dont get mad, get even" adage.Lets see how we can do that. Think...what does a phisher do with the information he gleans?He uses it ,of course. From reading other’s emails to emptying bank accounts, they do it all.
From a security perspective however, there is no such thing as foolproof security. Its just a matter of making it more difficult for the bad guy. So, in our attempt to get even with the phisher, that’s what we focus on. We try and make it difficult for him to use phished information. How?? We flood the phisher with junk data. Data that is trash, maybe randomly or dictionary generated. Once we flood the Phisher's database ( or whatever backend he is using) with trash, its like finding the proverbial needle in the haystack for the phish guy. Imagine having one valid victim credentials and ten thousand other garbage credentials.The only possible way for a phisher is to actually use the victim information to find out if its genuine.
Later in the article I demonstrate how such a thing maybe accomplished.
Surely, a more competent phisher will then possibly deploy countermeasures to such flooding.He may implement tracking , session or in extreme cases captchas in his phish site,.Maybe he will filter out the flooding IPs.We will probably think of a solution when they get there. Remember, I am talking about raising the bar. Not about eliminating the problem. Still, its not difficult to defeat such anti - antiphish countermeasures (Captchas would be an exception though)
Also, remember, I am not talking about protecting yourself from phishers, I am talking about making their life miserable enough to wean them away from it.
The inspiration for this comes from the hilarious 419eater.com
Now, as promised earlier lets look at how one may accomplish this.
Before I do that, there are some tools , libraries and utilities that I used, To name a few ,
The phish site:

Then I fire up my favorite :

Then I set my browser to use this proxy
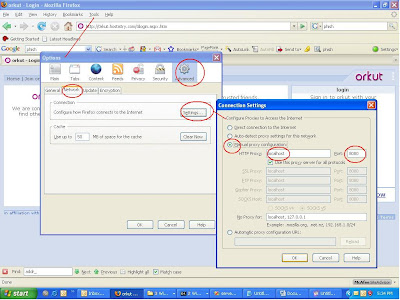
And then I get victimized

Here is what the phish request looks like:

Now there are many ways I can swamp this guy. I can do a quick and dirty command line ( ahh…isn’t curl great !!!), or , write my own C code using libcurl, or do a plain and simple perl script that uses libcurl binding.
I tried all three. But somehow, doesn’t seem to be a good idea to publish the code. I haven’t actually hosed the guy yet, I am in an ethical dilemma. Gunning down someone ,even if that person is a crook , is still a crime. Let me sleep over it
1 comment:
Hey, awesome post. Another option to direct spamming, is ofcourse just add that email to a nice spamlist. It'll save you loads of bandwidth and trouble as well :) .
Post a Comment