Friday, December 7, 2007
Computer security explained
This is the story I tell them:
One upon a time, there was this gentleman who saw a vast tract of land. He thought he would do something useful and productive with the land. He decided to setup a town there. He went to the king ( Microsoft ) and requested him to assign the land (Windows ) to him. The king agreed, albeit with a hefty monetary tribute, and named him governor of this town( granted him a license ). He also sent a few of his servants (programs like notepad, paintbrush ) who would let him get along smoothly.
The servants were trained for various purposes. While one was a good cook, the other was a good gardener, and likewise.
Soon, people started settling in this town ( data and programs ). Whenever the governor needed some special work done ( spreadsheet, word processor ), he would pay a handsome tribute to the king or his associates ( bought a license ) and ask them to send one of his specialist people( MSWord , Excel)
There were many other smaller towns around this town, some even in the neighboring kingdoms ( Other computers with different operating systems ). The neighboring towns were interconnected by good roads ( networking) and their people prospered with good trade and tourism ( advent of internet ). This got our governor thinking. He requested the king to build roads from his town neighboring towns. To use the roads, people needed chariots. The king's artisans made chariots and sold it to the governor.
However, people in another town built a nicer and cheap chariot ( Netscape). The king feared those chariots would rule the roads, and so, started giving away chariots for free ( Internet Explorer). To ensure that his chariot could run faster, he put charioteers in each chariot. These were no ordinary charioteers. They knew the way around the town very well. So much so, they could get the chariot right inside the governor's treasury, only if the passenger knew how and what to ask of the charioteer (Active X etc )
Now that the roads were getting a lot of varied traffic, the governor thought about managing it in a better way. The king had him designate each town gate ( port) for a specialized purpose to be manned by a specialized team( program using that port, like IIS using port 80 for a web server). So there was a gate which was used solely for moving agriculture produce The people manning the gates were trained by the king's people , and specialized in distinguishing good food grains from bad, and ensured that only the good stuff entered the town. (the programs responded to proper requests only) There was a different gate for household items, and a different one for tourists. ( like port 25 for SMTP email service , port 21 FTP file transfer service ),This led to a well organized system of entering the town for different purposes, and saved time and money for the visiting traders as well as residents.
However, local ironsmiths were having a hard time competing with cheap imports. They petitioned the governor and the governor ordered shutting down the iron trading gate. No one could now import iron into this town.
Some of the gates (like the pottery gate) were not used too much. Over the years the governor all but forgot about such gates. It just remained with the gatekeepers whiling away their time.
Now that roads had come up and chariots started to move around to neighboring towns and other places, the bandits in the forest around the town got interested in this town.(crackers) They hitched rides in the chariots that were going to or coming from the neighboring towns ( connection hijacking), befriended the charioteer (trust abuse), dumped the passenger , looked for any poorly manned gate (like our pottery gate ), fooled the gatekeepers, and sneaked in. Once in, they had the charioteer take them to the governor's treasury and decamped with his treasure. ( Computer compromised) The governor was irritated. He had the king create a moat (firewall) around his town, and had drawbridges installed. Only those gates which he explicitly permitted were to be allowed to be open and had their drawbridges lowered. ("default deny", allow selective access)
He also gave passphrases to all people in his town, and to all regular visitors and traders.(authentication)They were to speak out their passphrases aloud at the gate.If it was right, they were allowed in.
The bandits start arriving at the gate in hordes, and start saying out any and every phrase that existed/ they could think of. After many wild guesses, few of the guesses turned out to be right and the bandit who gave the right phrase could get in and steal stuff from the town(brute force ). To check this, he started issuing complicated long phrases in weird and foreign languages. Guessing the right phrase was still possible but would take a lot more time and effort (strong password)
The bandits then started eavesdropping on the visitor-gatekeeper exchange and steal the visitor's phrase to gain entry. To prevent this he started issuing non forgeable certificates to the traders(SSL certificates). He also installed a sound proof cabin at each gate so that the pass phrase cannot be heard outside (Encrypted communication). No one without the certificate was allowed to even attempt an entry. The system worked well till the time a lot of genuine but new traders start showing up. They were vital to the town's growth, but letting them in without proper validation was a risk. To help with this, he authorized 5 highly trusted people to setup offices in neighborhood towns and issue certificates to issue the non forgeable certificates to valid and genuine traders.( like Verisign and Thwate)
Of course, our governor had a huge and extended family living with him. The governor's relatives and family wielded as much power as the governor (privileged accounts), but unfortunately, some of them were quite gullible.
At times, the bandits succeeded in intercepting one of the governor's family members. They would befriend him, ride back to the town, have him call off the gate staff, and finally get fellow bandits in through the unguarded gates.
To counter this, the governed disempowered most of his relatives ( unprivileged user account). The gate staff would no longer obey them. For some of his work though, he still needed to empower some people, and he did empower a hand picked bunch of his loyal followers with various levels of authority (Selective access grant)
However, the governor soon discovered that some of the gate people had problems which prevented them from doing them job perfectly. For example, one of the gate manning teams had a person with a slight hearing disability, and another who had slight visual impairment (vulnerable programs) . Bandits could gain entry on this gate by displaying forged certificates and uttering words which sounded similar to the required phrase. (exploits)
Soon he discovered more problems with the gate people. Every time there was a problem with some gate person, the king would have that person examined, and if possible, help handling the problem.( patch releases)
Some of the bandits however were not interested in money. All they wanted was to vandalize the town (viruses). These bandits adopted a variety of ways to get in and wreak havoc. One would pose as a skilful mason, and when the governor let him in and asked him to work, the mason would wreck the town. One would pose as a beautiful dancer, enter the town and dig up the roads.
Fortunately, there were people in other kingdoms who knew these bandits by face (anti virus). The governor hired one of these people to protect his town. Every morning, the guard's kingdom's general sent him an album containing mug shots of newly discovered bandits (antivirus updates). That way, our guard was always up to date and knew of just about all vandal bandits.
Thursday, July 19, 2007
Pharming exposed
There are many variants of pharming. Here , in this article, I demonstrate one that is very easy to pull off by a beginner to moderate level attacker.
The attack leverages the fact that most ADSL modems run an http server for configuration, which is not secured
Most of the time, a guy from the phone company comes and installs the ADSL modem, and the user is all set. What they dont tell you is that you need to change the default password on your ADSL modem immediately.To drive home my point, I thought it better to put on my bad guy hat, and get to work.Please note that no actual breakin was attempted on any of the systems, and that information is provided for educational purposes only.
Assumptions:
You know how to set up a DNS and a HTTP server, and have your computer on the internet ( You will need to DMZ your own system if you are behind a ADSL router, and open up your firewall )
You know how to set up a gateway and enable IP forwarding on it.
Step 1: Reconnaissance
The first step is of course a reconnaissance attempt to find potential victims. I run a quick check for the world visible IP address my router has. I am lazy , so I simply visit showmyip.com. It shows me xxx.xxx.191.16
Not surprisingly, I am in my isp's address block.I just take a small sample of 255 systems in my vicinity, whose IP would be in the range xxx.xxx.191.1 to xxx.xxx.191.255
Now I need to find out which all DSL modems in this range are systems with default password.
I know that my ISP uses Beetel ,DLink and Huawei modems , which generally have admin as id and passwords range from 1234, password, admin,utstar.So, I write a program ( uses libcurl) which spawns 30 threads and tries each IP in the range with the default id and password.A scan of the 255 addressess takes me 3 minutes and shows me 14 open DSL modems
.The systems with 200 as HTTP response code will accept the default id and password (See figure below )
Here is a screenshot of my system discovery code ( He he he, the actual code that does the recon is not shown )
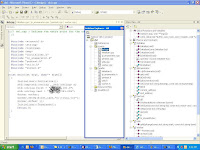
Click to enlarge: Code screenshot
If you have a dedicated system and unlimited data transfer, you can probably run this whole day to scan thousands of IP addresses.
Step 2: Preparing for the attack:
Now I need to decide what I want to do with these open systems. There are just too many things one can do with this. The possibilities ...I will explain later. For now, lets just say I want to grab those user's email id and password. For this, I can set up my own DNS, and put in authoritative entries for gmail, hotmail,yahoo, whatever I fancy. For all other domains, I simply forward them to my ISP's DNS. This is how it will work.

Click to enlarge: normal steady state DSL in operation
Once I have set up my DNS, I also need to put up a webserver to server those pages.
So, two major cavaets here are ,
1. To setup a DNS server
2. To setup a webserver with a DataBase at the backend to grab the user id and passwords
Step 3: The attack:
Though this step can be completely automated with scripts, or C programs,I do this manually with one single system, just as a matter of example:
The schematic of a DNS hijacking attack is shown below

So I login to this person's DSL modem, and point his DNS to my DNS server .And would you believe it??Thats all I need to do to grab this persons internet.
Logging in to the victim's router

Altering the DNS address

So that was easy, you could harvest a ton of stuff this way. But this doesnt give you much.So additional stuff can I try??Ummm..why not intercept ALL his traffic ?How ??Thats easy...set up your system to be gateway and do an IP forwarding
But then I want his whole system. Not just the traffic.Umm..OK, put his system on the DMZ. That way he is out in the open. I let nmap take shot at identifying what OS he os running, pull out a bunch of exploits and throw at this system , and presto...I have his computer.
But what will I do with his computer ? Will think about that later
Tuesday, July 17, 2007
Identifying Phish
If I were to identify Phish, the easiest way is to just take a look at the address bar, and check the site (Yeah, the phisher can put an image on the address bar , but that is easy to figure out).Another precaution is beware of wrong SSL certificates. These 2 prime measures seem to have been conveniently ignored.
Just have a look:
This is the original aol phish page:

This is siteadvisor's explanation:

Bank of America Phish analysis offered by siteadvisor

Capital One Phish analysis

Its surprising how a security company promotes such crude means to identify phish.
The sad part is that these guys seem to imply that a site with correct grammar and graphics is NOT a Phish site.Imagine what such inference does to the grandma class of users. This is unfortunate.
Thursday, July 12, 2007
PhishPhighting
True, other than try and steer clear of them ,there is little one can do for a phish attack.Surely, there are tons of advise on how to guard from phish.Whats more, security companies are making money out of identifying and flagging phish sites.
Now that makes me wonder...Is there no other go? Reminded me of the "dont get mad, get even" adage.Lets see how we can do that. Think...what does a phisher do with the information he gleans?He uses it ,of course. From reading other’s emails to emptying bank accounts, they do it all.
From a security perspective however, there is no such thing as foolproof security. Its just a matter of making it more difficult for the bad guy. So, in our attempt to get even with the phisher, that’s what we focus on. We try and make it difficult for him to use phished information. How?? We flood the phisher with junk data. Data that is trash, maybe randomly or dictionary generated. Once we flood the Phisher's database ( or whatever backend he is using) with trash, its like finding the proverbial needle in the haystack for the phish guy. Imagine having one valid victim credentials and ten thousand other garbage credentials.The only possible way for a phisher is to actually use the victim information to find out if its genuine.
Later in the article I demonstrate how such a thing maybe accomplished.
Surely, a more competent phisher will then possibly deploy countermeasures to such flooding.He may implement tracking , session or in extreme cases captchas in his phish site,.Maybe he will filter out the flooding IPs.We will probably think of a solution when they get there. Remember, I am talking about raising the bar. Not about eliminating the problem. Still, its not difficult to defeat such anti - antiphish countermeasures (Captchas would be an exception though)
Also, remember, I am not talking about protecting yourself from phishers, I am talking about making their life miserable enough to wean them away from it.
The inspiration for this comes from the hilarious 419eater.com
Now, as promised earlier lets look at how one may accomplish this.
Before I do that, there are some tools , libraries and utilities that I used, To name a few ,
The phish site:

Then I fire up my favorite :

Then I set my browser to use this proxy
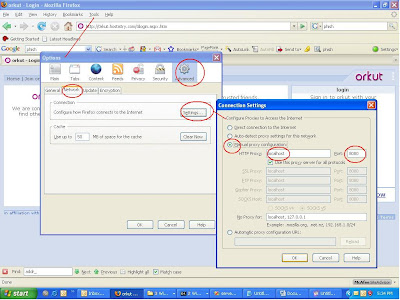
And then I get victimized

Here is what the phish request looks like:

Now there are many ways I can swamp this guy. I can do a quick and dirty command line ( ahh…isn’t curl great !!!), or , write my own C code using libcurl, or do a plain and simple perl script that uses libcurl binding.
I tried all three. But somehow, doesn’t seem to be a good idea to publish the code. I haven’t actually hosed the guy yet, I am in an ethical dilemma. Gunning down someone ,even if that person is a crook , is still a crime. Let me sleep over it
Monday, July 2, 2007
business emails on 3rd party webmail servers?
What bothers me is that this is not an one off isolated case. There are probably countless other instances where people are sending out sensitive business information over 3rd party public email severs.
It's probably a matter of time before someone comes up with a proposal for harvesting and profiting from sensitive data on email data centers.
Friday, June 29, 2007
The penetration tester
At the appointed time, the guy walks in, with a voluminous stack of printouts of emails from various sources crediting his work.
Boy...was I impressed.A guy with close to 8 years of experience, well versed with both black box and white box, with experience on security focused code reviews, a member of a web app security group, exploits under his belt and what not ...
Still, I need to talk to him , assess his competencies.So, I write a few lines of code that creates an SQL query string on the fly using a fixed sized stack buffer, and ask for a review.
And then the punishment began.
He identified the buffer overflow . I asked him to explain the working of a buffer overflow.I got a "are you stupid" stare, and my candidate went on tangentially about a tool which can detect all "unsafe" function calls, and report it.I prompted him to focus on the question, he goes on again on a remarkable tool that he used ( No, he wasnt the author of the tool, but an user) to discover web app security vulnerabilities. Well done, I said and moved on...
"Explain to me an XSS".He jumped to it. He explained.And I listened.We went to a site which had a blatant "staring you on the face" XSS. He explained to me again that he uses yet another "tool" for detecting XSS, and wont be able to answer my question without access to his tool.
But then, I do look for a possible flash of brilliance from people I interview. You can't expect people to know everything, can you? So, I go back to the code , and ask him how to mitigate the buffer overflow.
The contrived code was something like this
int userExists( const char *name)
{
char buffer[1024];
sprintf(buffer,"select * from users where name='%s'",name);
return runQuery(buffer);
}
Solution...replace sprintf with
memcpy(buffer,name, strlen(name) - 1);
At this stage, I had two options...thank him for his time and interest, or pull my hair out.
I still have hair on my head...
Resume padding can only get you an interview.Beyond that, you gotta know your stuff dude...
Tech Jargon
Me : I have to go now , Mary, I am scheduled to interview a guy.
Mary : Why don't you take up some of my work and let me interview the guy ?
Me : You can do an interview on "penetration testing" ??
Mary goes red in the face, looks embarrassed, and returns to her desk without replying.I wonder why.
Later in the day I realized . To the uninitiated, "penetration testing" seems to have a generous helping of sexual connotation.
I emailed her a wikipedia link which explains penetration testing :-)
Moral of the story: Do not use tech jargon in day to day life